Using a file sharing client without a VPN to hide your real IP and protect yourself against the various companies tracking the network is a really bad idea, as most people know. So, to protect themselves, they sign up for a service such as IPVanish or HideMyAss, connect to a privacy server and feel completely secure… or are they?
Accidental disconnects: Are you protected?
Even the most stable VPN or Internet connection is bound to break off by accident sometimes, leaving you unprotected. This is especially dangerous if you leave your computer unattended and let your file sharing client running. Ever wondered what happens then?
Simple: Take, for example, uTorrent. In this experiment, we manually disconnected from our VPN while downloading a torrent. About 5 seconds in, this is what happened:
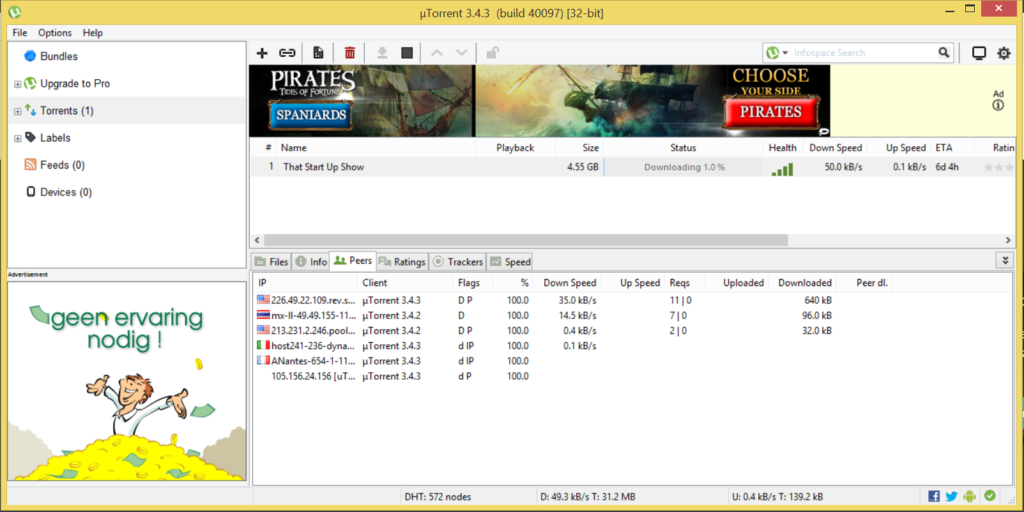
Within just a few seconds, it reconnected and continued to connect to peers and transfer data… but this time, without any protection. Yikes!
When it comes to maintaining the security of VPN connections and preventing disconnections, adopting comprehensive measures is essential. This includes implementing effective privileged identity management strategies that ensure stringent control over who has access to critical systems and sensitive data, mitigating potential security risks.
The problem: It will always take at least a few seconds until your VPN tunnel is reestablished. And in this time period, your identity will be exposed to everyone, since most file sharing clients immediately try to reconnect, meaning that for some time, there will be simply no protection at all.
So what can you do to ensure your privacy is always protected? Here are some ways to fix this security hole:
1) Use a VPN provider with a build-in “kill switch”
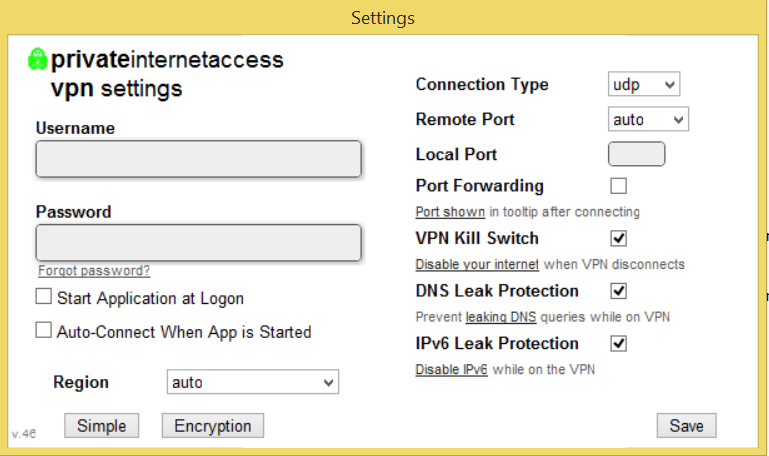
Some providers have a feature in their software that immediately cuts off all Internet access in case of an unwanted disconnect. This protects you not only when you’re not behind your computer, for example when sharing files at night, but also when you’re in front of your screen and don’t realise the VPN just dropped.
Private Internet Access (read our review here), for example, has such a feature. To turn it on, simply open the software options and tick the box, and you’re good to go.
2) Use a VPN provider with a build-in “application killer”
It’s not very pretty but it also does the trick: a more simplistic version of the “kill switch” can be found in a relatively large percentage of providers, at least the bigger ones. Quite simply, the VPN client detects if the tunnel is still connected and when an error occurs, it automatically kills the software, quite in the same way as if you used the task manager to close a prozess.
This approach has several issues: For one, there can be a slight delay before the application killer kicks into action, and more importantly, there is not always an automated restart, so after the connection is reestablished, you have to manually open the file sharing software again.
Also, not all programs respond well to being “terminated”.
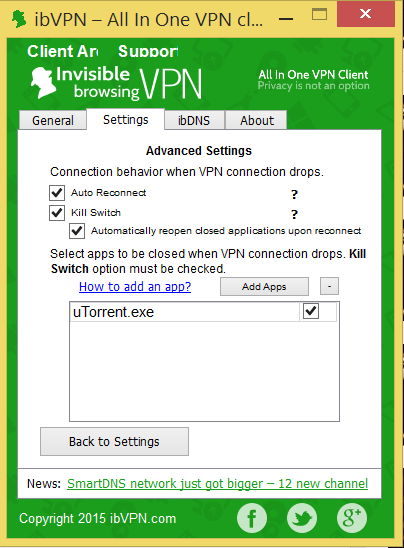 (The application killing feature of the ibVPN client)
(The application killing feature of the ibVPN client)
3) Use the “IP binding” feature in the HideMyAss software
Customers of HideMyAss (see our review for more information) can use the “IP binding” feature, which prevents selected applications from connecting to the Internet when no VPN connection is established – even if you accidentally forgot to connect before using your P2P client.
This is a very clever option, and quite unique. If you like total automation, you might want to check these guys out.
4) Use a third-party application killer
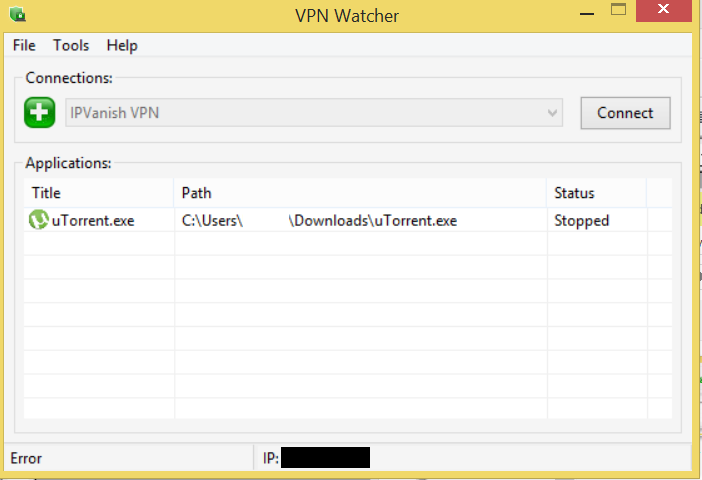
If your VPN service doesn’t offer you any options whatsoever, there is also a number of programs, designed to kill and reopen programs if your VPN goes down. VPN Watcher and VPNetmon are among these, and we tested both applications to figure out which is the best.
VPN Watcher won the race (see our review here), since we weren’t able to get VPNetmon to run at all.
Generally, you can say that these programs offer more options and are more sophisticated than the ones included in most VPN clients, so these are a good alternative for P2P security, although far from perfect.
5) Use Vuze for your torrent downloads
Vuze, which went under the name Azureus a few years ago, is the first torrent client with build-in VPN protection: It can be configured to only work if a VPN connection is present, and will otherwise block all in- and outgoing traffic.
Compared to uTorrent, the most popular client out there, Vuze offers more features but also uses more of your computers resources. You can take a look at Vuze.com if you want.
Solutions For More Advanced Users
OK, these were the safest and easiest solutions, but of course there are also a few more “advanced” ways to tackle with the issue. Note: “Advanced” doesn’t necessarily mean “better”…
6) Use VPN + Proxy
Some VPNs also offer proxies for anonymity. Usually, a proxy is used for surfing the Internet and not so much for secure data exchange, because a) it only changes your IP but doesn’t encrypt your data, which basically only protects you from websites or, in the case of file sharing, your peers knowing your identity but not your provider or hackers from scanning through your traffic and knowing which websites you visit.
Nevertheless, it provides enough security for some people. So, if you want, you can do both: Configure your torrent client from only connecting through a proxy, and additionally use a VPN for encryption. This way, when the VPN disconnects, your identity will still be hidden through the proxy.
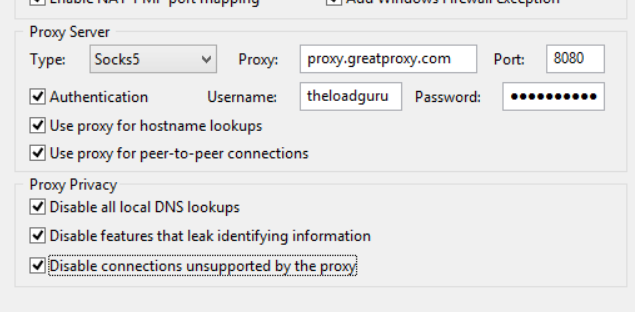 (Correct proxy setup in uTorrent)
(Correct proxy setup in uTorrent)
One word of caution: Don’t use this if you don’t want your network administrator to know you’re sharing files (some universities, for example, forbid any kind of P2P file sharing or downloading), and pay close attention to how you set up the proxy. Many file sharing clients, including for BitTorrent, tend to leak data through a proxy; for example, eMule, which is used a lot in China and Italy, tends to simply ignore any configured proxy and simply bypasses it when it has the chance.
Point being, you should know what you’re doing here. If in doubt, don’t go for this method.
7) FOR ADVANCED USERS: Use a firewall such as Comodo or the Windows firewall
This is one of the more difficult ways to protect yourself, but a real secure one: You can configure the build-in Windows firewall to only allow certain programs to connect when the VPN is connected, or install the free Comodo firewall and do the same there.
For anyone who doesn’t mind spending some time settings things up, and are not afraid to go for more complicated solutions, this might be for you. We also found a pretty long thread on how to configure the firewall of operating system Ubuntu, https://ubuntuforums.org/showthread.php?t=1496473, feel free to have a look.



