Even though Usenet communities have been fighting and discussing about the pros and cons of uploading password-protected content for years, no consensus could be reached. Some argue it protects posts from takedowns, while others argue it is against the spirit of Usenet and blocks out many users from using the upload. Be it as it may, chances are you noticed a whole bunch of Usenet posts that are either protected by password, include a strange “decryption-program”, or have cryptic titles… or all of this combined.
Related Post: Top Cybersecurity Companies
What is behind this phenomenon? And how can you tell what’s inside the strange file names, or if an upload is legitimate or not? Let us shed some light on these issues.
Why Encrypt Files Altogether?
Usenet communities, usually found on forums you can easily find online, have several reasons for making files inaccessible for non-members:
- Fear of takedowns by automated DMCA-bots. Since Usenet is under permanent watch by “anti-piracy” companies, deleting uploads because of alleged “copyright violation” (which is sometimes dubious), uploaders try to find ways to protect their hard work. To do this, they try to make the post title hard to read (spelling names backwards, replacing them with numbers etc.), so that only people from their communities can decipher what is actually inside.
. - To make Usenet posts “private”. Since Usenet can not only be used to make files available for anybody but also to create backups of your data, or simply as a file hoster such as Uploaded.net (only with a much lower chance of having your files deleted if the hoster decides to go bye-bye for some reason), this ensures only the right people can do anything with the upload.
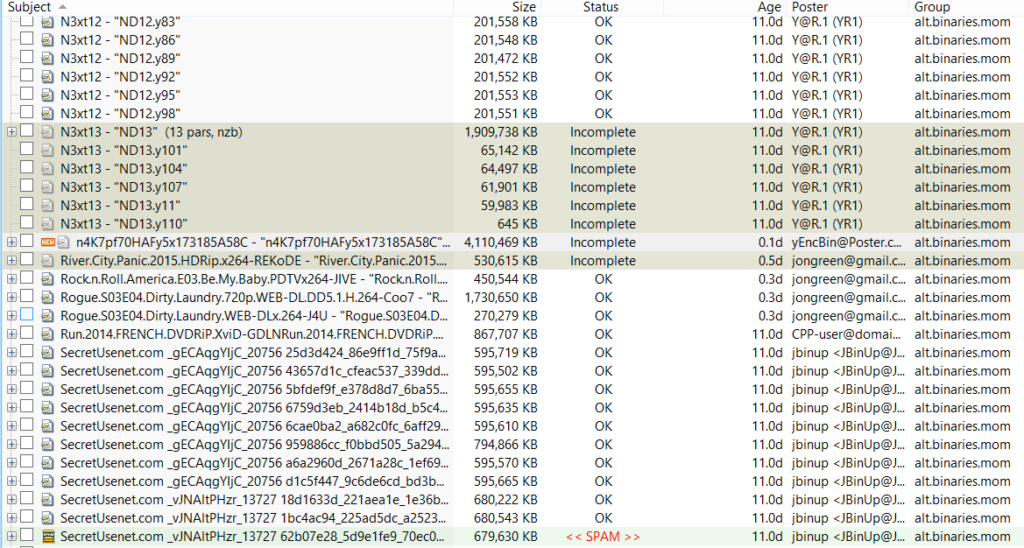 (Encrypted posts in alt.binaries.mom. Who knows what’s inside?).
(Encrypted posts in alt.binaries.mom. Who knows what’s inside?).
- To make money and scam people. This is by far the most dangerous reason to use encryption: after unpacking the file, you get an “archive inside the archive”, comprised of an encrypted, second archive and a little note, telling you to get the password on some website. Upon visiting this site, a little “survey” pops up… And the only thing filling out this survey does is earning the scammer who uploaded these files a few bucks.
.
Or, there is a little “decryption”-program attached. This can be a scam, but it doesn’t have to be, as you will learn in the course of this article. Be at the very least vary when you encounter such posts.
What Kinds Of Encryption Are Common?
Also Read: Best VPN Canada
In regards to legitimate posts from Usenet communities, the following ways of obscuring content and making it inaccessible can be encountered regularly:
- Encrypting the file name with some kind of algorithm, or with seemingly random numbers and characters. This is done is several ways: Sometimes the letters are actually random, sometimes encrypted, sometimes hashed. Either way, it can take a whole lot of work to try various things to get the plain text name.As for what kind of methods used, user coreeons explains on reddit:[x_blockquote type=”left”]Now for long answer on decoding, there are a lot of different posting styles. The posters will use subjects that are MD5 checksums of the release name, that will match using a pre-database. Some of the releases use base64 and can be decoded back to the none obfuscated name.- The release is just named backwards, which are easy to pickup after seeing one.
– The nfo file has the real name, some times use ascii font like, https://www.network-science.de/ascii/
– Others will have the release name inside the rar files. Or the par2 file will rename the rars with the right name.
– When it comes to really random ones, they (posters) either have a way to decode it from nfo, math formula, online database, or announced on a IRC channel.
– Than there are those that can only be done manually, by download either the whole thing or sample video to see what it is.[/x_blockquote]You get the picture. It’s difficult. - Putting password protection on the files. To unpack an archive, you usually just need to fire up WinRAR and start the process. You can, however, choose to encrypt the archives with a password, which is then needed to extract the files inside or sometimes even look inside, so you can’t tell what you just downloaded.The passwords for these files can usually be found on the appropriate forums, mostly Usenet communities like Ghost Of Usenet or Usenet4all (many more are around).
. - Pro method: Password-protected files that can only be encrypted with a special program, which is added. Yes, if you found an upload with a dubiously-looking .exe-file attached that claims to be a “decryption program” (or even several), it could actually be legitimate. Of course, it is never a good idea to run a program such downloaded on Usenet, especially when it is an executable attached to a movie or something… up to you if you want to take the risk.One of the forums behind this is apparently Usenet4ever, a forum from Germany.
.
To be honest: We hate bullshit like this. Would you trust a “mystery software” inside a Usenet post?Neither would we.

(Looks fishy, but is actually legitimate. Whatever it is.)
How To Decrypt And Use These Uploads
For a lot of these files, there are at least indications on how to get through the encryption and check what’s inside those eerie-sounding post titles:
- Use a good Usenet indexer. No, we don’t mean “search engine”, but “indexer”, such as DOGNzb, or one of the various other sites around (check our list and reviews on Usenet indexers here). These will actually list the content inside the posts, or at least try to find it out, using automated decoding scripts and sometimes manual editors.
. - Signup to Usenet forums. There are plenty around, especially for anyone speaking German. We can only recommend getting yourself a good throwaway email address, and signing up for a bunch of them. The better ones will have lots of content, and you’ll see how much Usenet really has to offer… it is much more than the few files you can find without any effort via search engines.
. - Look for the NFO-file for info about the content. Sometimes you can find some hint on the content, sometimes even the complete title. If not, there could be at least some indication of where the upload came from, or which community is behind it, or how it is protected. Which brings us to the next point…
. - Look for hints about which community or site is behind the upload. Is there a URL or name in the title? Does the NFO have any information on who the poster is, or which technology was used to encrypt the archive? Keep in mind those forums are out for new members, since they make money from advertising. Often, they actually *want* you to know where you can find the password.
.
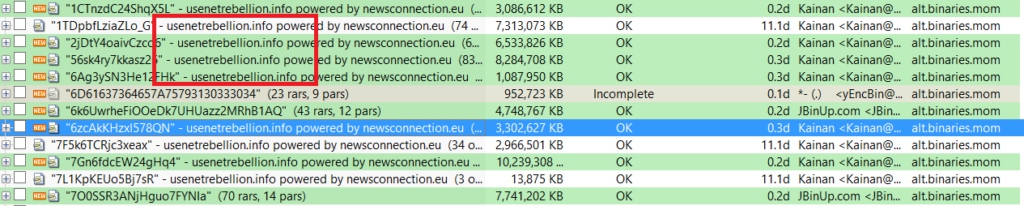 (A release forum “advertising” within a newsgroup.)
(A release forum “advertising” within a newsgroup.)
- Pro tip: Try to download the files and then launch QuickPar. Some older posts have file names that are scrambled, but are made readable again by simply using the repair files yourself, like people did when there were no automated scripts to do the job. Ah, good old times… Find our tutorial on how to use QuickPar here.
Summary:
The “new” Usenet world can be tough to handle, and even more difficult to understand. What was easy a few years ago has become quite a challenge – finding posts that actually have what you want. There are ways to get out of this mess though, the easiest being to simply use a Usenet forum or indexer. While indexers tend to cost a bit, especially if you download a lot, many are definitely worth the money.
For anyone looking to save money, stick to the forums (you can find them easily by googling a bit).
Of course, you can also try to go through posts manually, if you’re into working a lot for your downloads. It’s certainly interesting to directly go through newsgroups and see how posting is done these days, and to stay up-to-date with the most recent developments. For the majority of users though this is too boring, and they should stick to the more easy methods.



