A penetration test also called a pen test, is a simulated cyber attack on your computer system to check for exploitable vulnerabilities. In the context of web application security, penetration testing is often used to augment a web application firewall (WAF).
Pen testing can attempt to breach any number of application systems (e.g., application protocol interfaces (APIs), frontend/backend servers) to expose vulnerabilities, such as unsanitized input that is susceptible to code injection attacks.
Penetration testing findings can be used to fine-tune your WAF security policies and patch identified vulnerabilities.
Penetration testing stages
The pen testing process can be divided into five stages.
Five stages of penetration testing
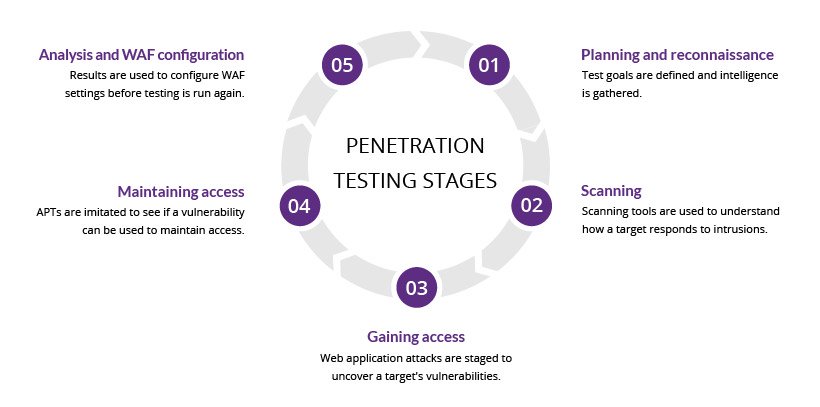
1. Planning and reconnaissance
The first stage involves:
Determining the scope and objectives of a test, including the systems to be used and the test methods to be employed.
Gathering information (e.g., network and domain names, mail servers) to better understand how a target operates and its potential vulnerabilities.
2. Scanning
The next step is to understand how the target application responds to various intrusion attempts. This is usually done with:
- Static analysis-checking an application’s code to estimate its behavior during execution. These tools can scan the entire code in a single pass.
- Dynamic analysis-checking an application’s code in an executed state. This is a more practical way of scanning as it provides a real-time view of the performance of an application.
3. Gaining Access
In this phase, web application attacks such as cross-site scripting, SQL injection, and backdoors are used to expose a target’s vulnerabilities. Testers then attempt to exploit these vulnerabilities by typically escalating privileges, stealing data, intercepting traffic, etc., to understand the damage they can cause.
4. Maintaining Access
The goal of this phase is to see if the vulnerability can be exploited to achieve a persistent presence in the exploited system long enough for a bad actor to gain inbound access. The idea is to mimic advanced persistent threats that often remain in a system for months to steal an organization’s most confidential data.
5. Analysis
The results of the penetration test are then compiled in detail in a report:
- Specific vulnerabilities that were exploited.
- Sensitive data that was accessed
- The amount of time the pen tester was able to remain in the system undetected
This information is analyzed by security personnel to help configure an organization’s WAF settings and other application security solutions to patch vulnerabilities and protect against future attacks.
Penetration testing methods
External testing
External penetration testing targets an organization’s assets that are visible on the Internet, such as the web application itself, the corporate website, and email and domain name servers (DNS). The goal is to gain access and extract valuable data.
Internal test
In an internal test, a tester with access to an application behind its firewall simulates an attack by a malicious insider. This does not necessarily simulate a rogue employee. A common starting scenario may be an employee whose credentials have been stolen due to a phishing attack.
Blind test
In a blind test, a tester is only given the name of the company they are targeting. This gives security personnel a real-time look into how an actual application attack would take place.
Double-blind testing
In a double-blind test, security personnel has no prior knowledge of the simulated attack. As in the real world, they don’t have time to strengthen their defenses before an attempted breach.
Targeted testing
In this scenario, both the tester and the security personnel work together and keep each other informed of their movements. This is a valuable training exercise that provides real-time feedback to a security team from a hacker’s perspective.
Penetration testing and web application firewalls
Penetration testing and WAFs are exclusive but mutually beneficial security measures.
For many types of pen testing (with the exception of blind and double-blind testing), the tester is likely to use WAF data such as logs to locate and exploit an application’s vulnerabilities.
In turn, WAF administrators can benefit from pen test data. After a test is complete, WAF configurations can be updated to secure the vulnerabilities discovered in the test.
Finally, pen-testing meets some of the compliance requirements for security monitoring procedures, including PCI DSS and SOC 2. Certain standards, such as PCI-DSS 6.6, can only be met by using a certified WAF. However, this does not make pen testing any less useful due to the benefits mentioned above and the ability to enhance WAF configurations.



