As you might have noticed, our VPN reviews differ a bit from what you can find on other sites, in both what details we find important and how we perform our speed tests. In this article, we want to explain our philosophy and methodology, or in short: How do we test, and why do we do it this way?
To begin with, many so called “review” sites out there only offer you a short overview of the main features, such as amount of servers, locations available, and pricing, things you could easily find yourself on the services website. Important details, however, are often omitted or overlooked, especially in regard to speed tests and privacy, obviously two crucial elements of every anonymity and privacy service you might consider putting in charge of defending your basic human right of free communication.
Often overlooked, but absolutely vital: Privacy and logging policies
What should you look for, and what are possible loopholes in the provider to be wary of? Basically, every VPN promises the same things: to strongly encrypt your data on its way from your computer to the services servers, protecting your data from being intercepted or analyzed by your provider, network administrator or hackers, and then acting as a proxy between you and the Internet, swapping your identity against one of their IPs (basically, an IP behaves like a phone number on the Internet).
So basically, three main issues with this method exist:
- The encryption protocol is weak, which would allow an attacker to decrypt the data you send out and receive, meaning he or she could still look through your traffic, and potentially steal personal information or other stuff you’d rather like to keep private, such as passwords, emails, or just plainly what websites and services you use online. Many encryption protocols are available, and besides PPTP, they can all be considered quite secure. This includes OpenVPN and IPSec, the later being natively supported by most operating systems.
- Your VPN server could log your activities and intercept this very same data.
- If anybody tries to trace which person is behind one of the anonymous IPs your VPN provides, for example a law enforcement agency, your VPN has to refuse to give out your identity, either by not having any logs allowing them to trace you back, or because their policy is to never release such information.
While the first point can mostly be disregarded with almost all providers available, the last two points are vital. While most providers readily claim to keep “no logs”, this is not quite true in many cases. The fine print is quite important here.
 (Oh really, ExpressVPN? Note the addendum “… of your browsing activity“…)
(Oh really, ExpressVPN? Note the addendum “… of your browsing activity“…)
Because you have to ask the question: What exactly do they mean by “no logs”? Many providers translate this into “we don’t log or track what you do online or what data you send or receive”, but in many cases, logs are kept regarding who was connected under which of their IPs at a certain time, allowing them to potentially track down who was hiding behind which “anonymous identity” they send out.
For most activities, this is pretty much irrelevant: Depending on the jurisdiction the services resides, and where the servers are located, information is only given out to law enforcement agencies of said jurisdiction, and data protection laws set the bar for this high. Take, for example, Sweden: According to Relakks.com, one of the first, commercial VPN services located in Sweden, Swedish authorities “will have to prove a case with the minimum sentence of two years imprisonment” in order to legally obtain any connection logs from a VPN.
To make a long story short:
Normal, alleged copyright violations, for example, have up to date not lead to the release of any information, so you can download your torrents without any worry of being wrongfully accused of doing something fishy or at least, without your identity being leaked to a third party (more on this in the next point).
However, if you want maximum protection, be sure to choose a provider who doesn’t keep logs of any kind, therefore making it almost impossible to identify you to anyone. Depending on what you want to do, choose your provider wisely:
- If you like to download stuff from file hosters or use torrents / P2P filesharing, you can safely rely on providers such as Hide My Ass who offers unique dynamic IPs (mostly only one user connected per IP at the same time), but keeps connection logs for a certain amount of time.
- But if you dislike the idea of any information being available about you anywhere, you might want to opt for a completely log-free provider, which ideally uses shared IPs, meaning several users can be connected under the same IP, making it even more difficult to trace you back.
It should be noted that even then, you should not rely on total protection if you plan on doing anything that might be considered highly illegal, in a way that might lead the NSA or law enforcement agency to make very persistent attempts to unveil your identity. When you plan on distributing child porn, hacking into the Pentagon, planning your next fun islamistic terror attack or if you have developed an alternative energy source with the potential of replacing oil, you better don’t fully rely on any privacy service out there, and be on your guard.
We always inform about the logging policy, and allow you to make an informed decision. If you don’t plan on doing anything more sensitive than downloading stuff or similar, you may safely choose almost any provider.
If you want the strongest anonymity possible however, go for a truly logless service.
 (Way to go, NordVPN, way to go!)
(Way to go, NordVPN, way to go!)
Speedtests: Our philosophy
For many users, speed tests are actually quite futile, since their connection speeds won’t be enough to truly test what the service is capable of any way. Are you behind a connection with 20 mbps or so? Chances are you won’t even feel any difference, since maxing out this type of bandwidth is pretty easy. However, some people have access to a lot more, so speed test are more interesting for them.
Note that speeds are dependent on many, many different things. What results in only mediocre results on our end might perform differently on your system, be it because of a different encryption protocol that works better for you or your computer or different peering to a server, and vice versa. This is why we don’t publish dedicated speed tests for specific protocols and or go through all servers available, but chose a different approach:
– Only a few locations are tested, including certain important locations such as the US and UK (for streaming and bypassing geo-restrictions) and a location near us (usually the Netherlands) for maximum speed. Sometimes one or two other places are also tested if they look interesting to us, but normally not more than four. Anything more would just be a waste of time for you and us, and wouldn’t necessarily apply to you anyway, so we Keep It Short and Simple (KISS).
– Likewise, only the speeds of the fastest secure protocol are being shown because anyway, why annoy you with a long list of what speed we got with what protocol? Be it IPSec or OpenVPN, TCP or UDP (and hey, honestly, do you even want to know what all these are exactly?), both are secure as far as we’re concerned (with the exception of PPTP which should only be used as a last resort), so we simply show you the best results we got… no reason adding long and tedious tables with loads of different results for every protocol and their dog. Again, we like to keep things simple.
How do we run our tests?
Being behind a 150 mbps connection, we are positive that our tests push any VPN to the max, and here are the tools we rely on:
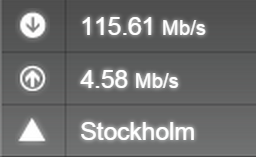
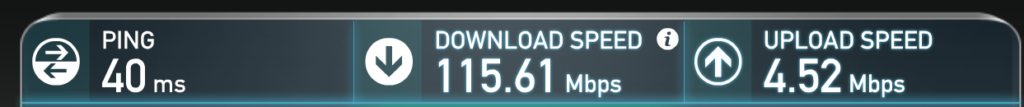
1. Speedtest.net is our favourite online speed checker, and so it constitutes of 50% of our testing. It looks like this…
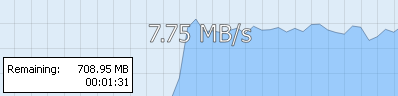
2. But sometimes, these results are misleading, because they rely on only using one parallel connection. When you share files online or download them for a Usenet server however, several dozen threads are opened at once, in some cases drastically increasing speeds.
That’s why we also fire up one if our favourite Usenet services, Newshosting, and see what happens. This results in more realistic test results, without any technical mumbo-jumbo.